The stability and effectiveness of modern military and civilian infrastructures rely fundamentally on robust communication networks. As warfare increasingly moves into digital spaces, these networks become critical targets
for cyber-attacks, highlighting vulnerabilities that, if exploited, can yield devastating strategic consequences. Cyber-attacks on communication networks involve deliberate and malicious activities intended to disrupt,
degrade, or entirely disable the channels vital for military command, civilian coordination, and societal functionality. Understanding this phenomenon is essential to appreciate both its tactical use and potential threats
posed to national security and everyday life.
Communication networks, including satellite systems, telecommunications, and internet infrastructures, form the backbone of contemporary strategic operations. These
systems enable rapid and secure exchange of information necessary for operational decision-making, intelligence gathering, and logistical coordination in warfare scenarios. Their disruption can significantly impair a nation's
ability to respond to crises, sustain defensive measures, and maintain civilian safety and morale.
Cyber-attacks on communication networks encompass a variety of methods designed to impair or eliminate a network's capacity to function properly. These attacks range from relatively straightforward disruptions, such as denial-of-service (DoS) attacks that temporarily overwhelm networks, to highly sophisticated infiltrations deploying advanced malware, spyware, ransomware, and wiper software. Each type of attack has unique implications, yet they collectively aim to compromise the integrity, confidentiality, or availability of information critical to national defense and societal stability.
The roots of cyber warfare date back decades, as digital technologies and the internet expanded. Cyber-attacks at first were elementary, such as in the form of intrusions into servers or defacements of public-facing websites,
motivated by political statements or low-grade espionage. But as digital communication grew in reliance, so did the complexity, scale, and strategic motivation of cyber-attacks.
The advent of the new millennium was
marked by the transition as states identified cyberspace as integral to state power. The 2007 Estonian cyber-attack demonstrated how organized cyber activity could destabilize the communication infrastructure of nations,
impacting government, banking, and media services.
Subsequent years saw ever-more targeted and sophisticated assaults. The NotPetya ransomware attack of 2017, which was most commonly attributed to Russian actors,
demonstrated the scale of disruption possible, crippling crucial networks and generating billions in damages. Nation-state operations, like the Andariel group from North Korea, focusing on military communication networks,
demonstrated the military aspect of threats in cyberspace. The operations of these organizations have involved large-scale espionage, garnering highly sensitive data regarding satellite technologies as well as communication
protocols.
Today, the strategic importance of cyber-attacks on communication networks is evident through ongoing global conflicts. The Russian invasion of Ukraine in 2022 vividly demonstrated this. In a coordinated effort, Russia executed
a significant cyber-attack against Viasat's KA-SAT satellite network, employing a specialized wiper malware called "AcidRain." This attack directly targeted Ukraine’s military communication capabilities but also inadvertently
affected tens of thousands of civilians across Europe, illustrating the indiscriminate nature of cyber warfare and its widespread consequences.
Additionally, North Korean cyber operations have repeatedly targeted
defense, aerospace, and satellite communication technologies globally. Such attacks not only aim at espionage, extracting valuable intellectual property, but also sabotage, aiming to weaken adversaries strategically by
disrupting their military communication infrastructures.
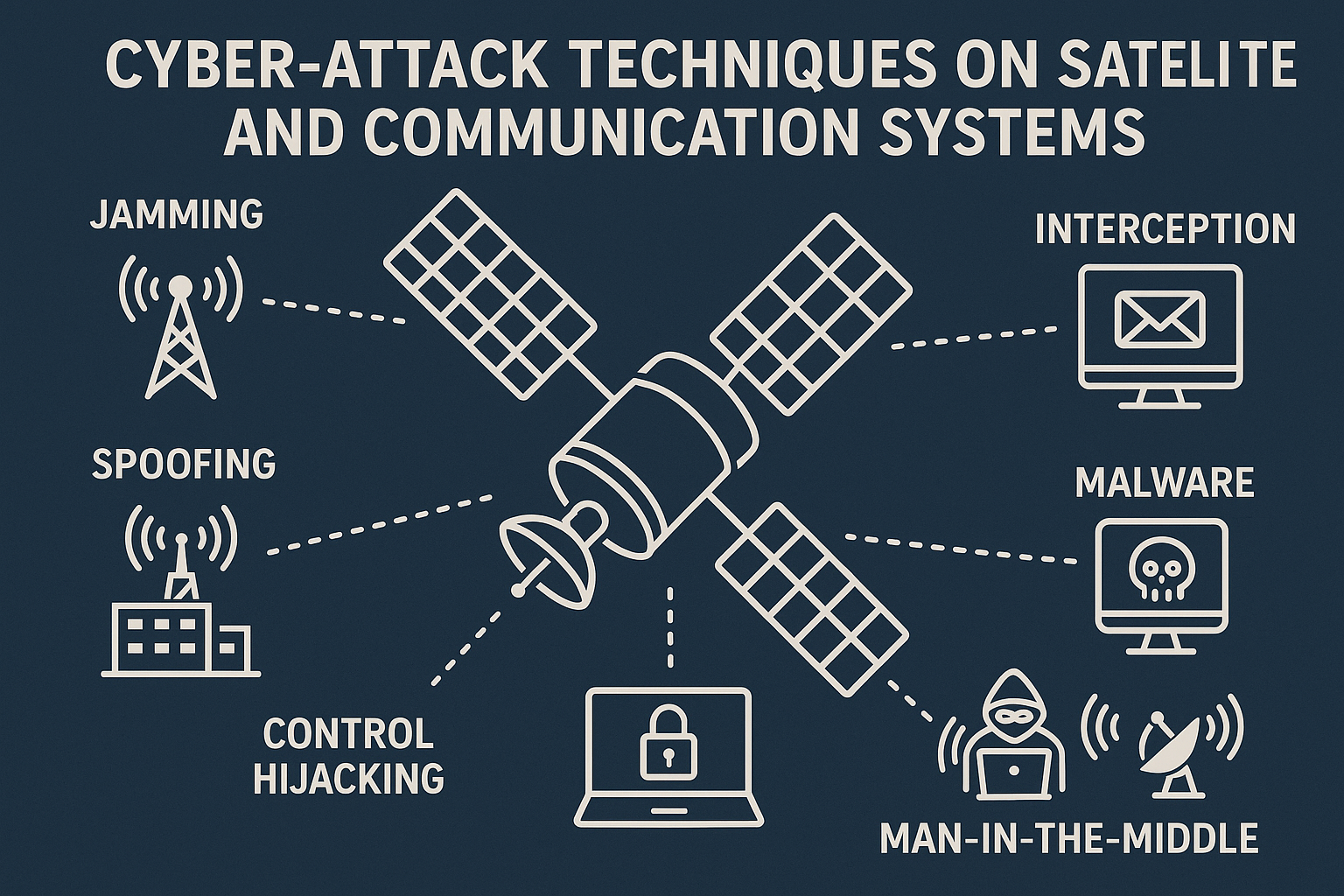
The methods employed in cyber-attacks are diverse and highly adaptive, leveraging a combination of technological vulnerabilities and human weaknesses:
A clear understanding of cyber-attacks on communication networks can be reinforced through visual aids. For instance, a comprehensive infographic can depict the typical progression of a cyber-attack:
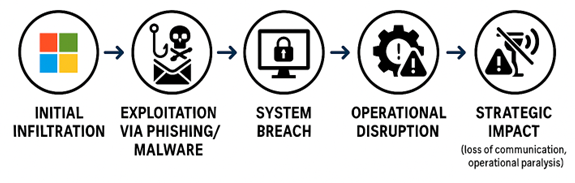
Such visual representations clarify how attackers systematically compromise networks and underscore the critical importance of strengthening cybersecurity measures to protect communication infrastructure.